What is CVE-2020-0796 (aka SMBGhost) vulnerability?
tl;dr – Microsoft has released an out-of-band patch for the issue already which is being rolled out via Windows updates. If automatic updates is not the way you perform patching, you can download the patches manually from Microsoft’s page.
A remote code execution vulnerability in SMBv3 protocol (enabled in the latest Windows versions) was announced by Microsoft on March 10, 2020. As initially stated, but then removed by Microsoft itself, the vulnerability is wormable, which means that a specially prepared malware COULD automatically spread across the network infecting and completely compromising vulnerable systems.
How important is it?
Since currently there is little technical information, the likelihood of immediate mass scale exploitation is low. However, since the technical details point to the exact version of Microsoft Server Message Block protocol and functionality (compression feature) it is likely that hackers and intelligence services are already working on ways to create a working exploit. Once the exploit is available, it could give full system access to the vulnerable system.
To better understand the impact of a wormable bug in a major operating system it is useful to remember bugs like EternalBlue (weaponized by WannaCry and NotPetya), BlueKeep and the classical MS08-067 with its companion Conficker.
Those who prefer videos, just watch this video.
Are you affected?
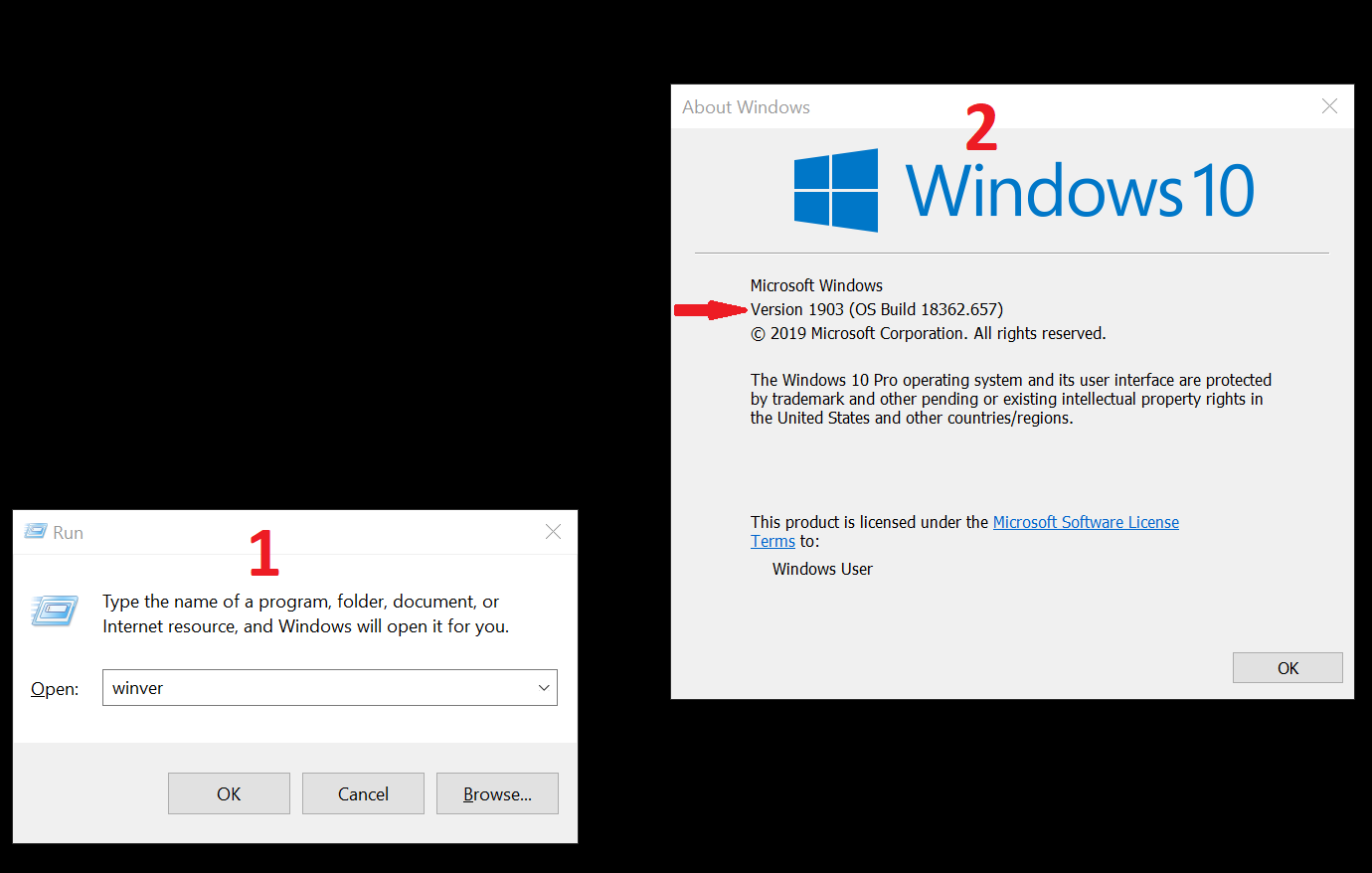
Microsoft Windows 10 and Windows Server versions 1903 and 1909 are affected in their default configuration. To find out which version of Windows 10 or Windows Server you are running simply execute “winver” from the command line or “Run” dialog (Win + R).
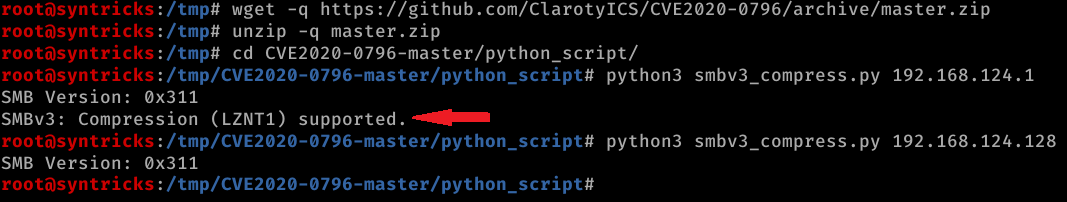
While some of the tools for automatic detection of potentially affected systems are already in the wild, it is important to understand that support of SMBv3.11 is not a definite confirmation of insecure configuration. The target system MUST have compression feature enabled (which is the case in a default configuration).
Currently, the tools form @Claroty can be used to perform initial analysis.
For large scale checks we recommend nmap scans.

According to analysis performed by some researchers ~48000 systems might be exploited from the Internet.
We’ve just finished our first internet wide scan for CVE-2020-0796 and have identified 48000 vulnerable hosts. We’ll be loading this data into Telltale for CERTs and organisations to action. We’re also working on a blog post with more details (after patch).
— Kryptos Logic (@kryptoslogic) March 12, 2020
What to do next?
There is an official patch from Microsoft already which is also being rolled out already world wide (via Microsoft Windows update mechanism).
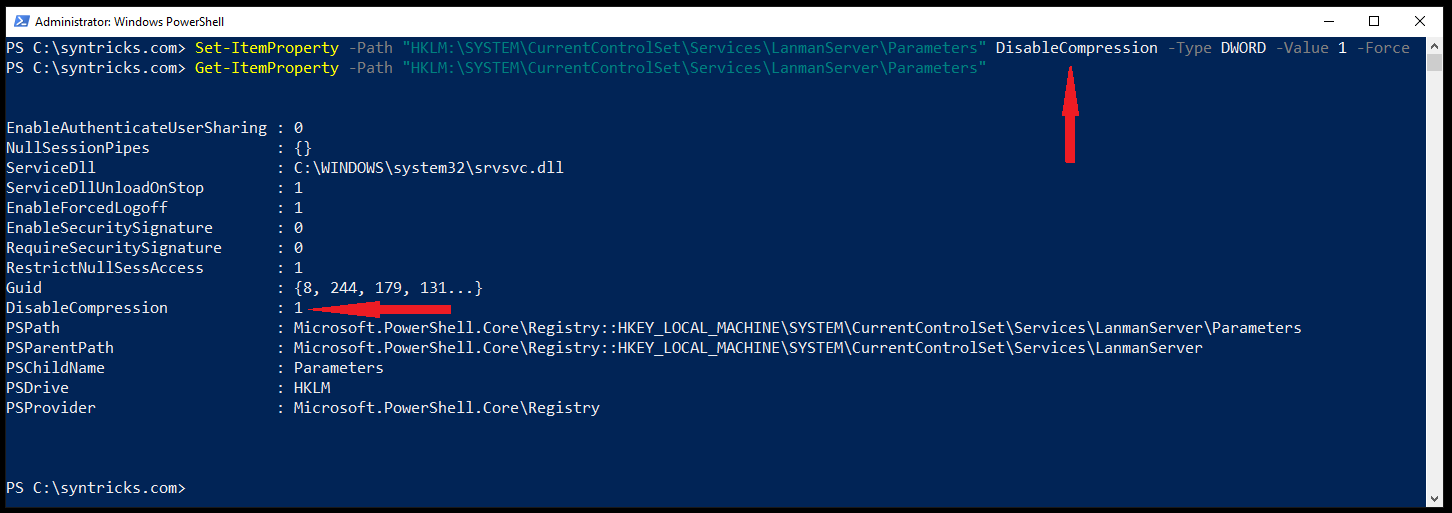
Sometimes applying patches might break stuff due to quality issues (lack of sufficient testing of the patch before a wide roll out). Therefore, a workaround which should help can be used. By executing the following command under administrator privileges the affected compression feature can be disabled.
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" DisableCompression -Type DWORD -Value 1 -Force
Additionally, tightening firewalls for port 445 can be performed. Finally, the Blue team of your company should pay attention to Windows security logs for anomalies (service deployments, new user creations, crashes, suspicious logon events, etc.)
Tech stuff
You can read an in-depth analysis of the bug here.
Denial of Service examples are already available in the wild.
A Local Privilege Exploit is available here.
Stay Safe!


